-
Recent Posts
Recent Comments
Archives
April 2024 M T W T F S S 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30
Intelligent Systems (AI Progress)
- WEEK 5
This focuses on team selection, roles and deciding on what to work on for our final project. Our group/team consists of 3 members namely:
– Edbert
– Jordy
– and myself (Lamin)
Project proposal : At initial, we decided to do a project based on Facial Recognition as it was the only idea we got regarding Artificial Intelligence. However, some of the other students were also thinking of working on similar project so we decided to shift to something else in order to have a unique project. As we were all out of ideas, we decided a self homework i.e. to do a research on AI then bring our ideas together on the next session.
- WEEK 6
In this week, we focused mainly on our final project idea. We did a research on various artificial intelligent contents in order to come up with a deep understanding of AI and in what area of computer vision we can focus on. After a couple of research, we decided to work on “Object Recognition” project. We chose the idea because Object Recognition opens new paradigm for computer applications. Object Recognition is now implemented in smart phones, e-commerce and smart cars. With the idea, we decided to do one.
- WEEK 7
In this session, we expanded our research on “Object Recognition” and gather more information on useful programming libraries we can rely on to get the work done.
To get this project done, below were the list of basic library requirements for the project based on our research:
– Numpy
– Matplotlib
– OpenCV
- WEEK 8
We focus on executing simple projects based on the libraries recommended to use. However it wasn’t as easy task because everyone in the team is using/running different operating system and package manager. As a Linux Fedora user and conda as my package manager, it took me almost the whole session just to figure out how to install some packages and also dependencies libraries like:
– Python-devel
– cmake
– gcc g++
– libpng-dev
– libjpeg-dev
– libopenexr-dev
– libtiff-dev
– libwebp-dev etc
However, I ended up installing all the required dependencies and library to proceed.
- Week 9
For this week, we have already got all the requirements for the project. We split our soles to work on different segments of the project. Since our project is based on Object Recognition, we need to find objects to work with, classify the objects and train our model. Each of us focused on one segment while we work collectively. Again, we all did our research on the various task we are to work on to finally start our project during the next meet up.
- Week 10
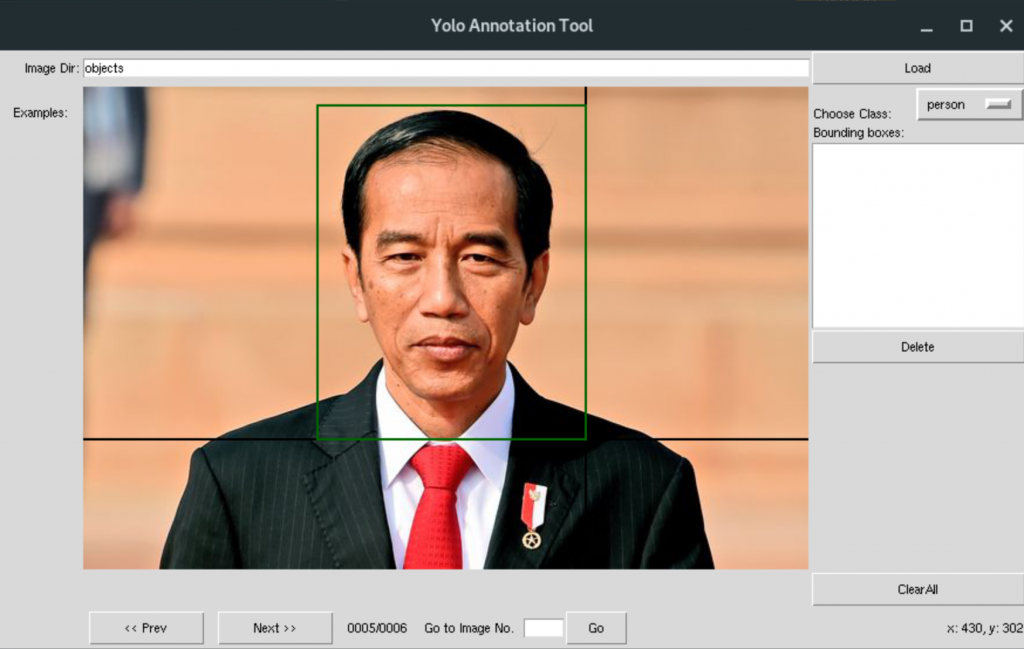
During the week, we started to classify our objects, implement the python code and train our model. Our project is based on “Yolo” which is an extreme fast real time multiple object detection algorithm. The algorithm looks at an object once and identify the list of classes e.g in a classroom photo, it can identify person(students), seats, tables, books etc i.e. if trained as classes or object. In order to achieve a good result, we need to identify the list of objects in a photo or image file as class. Since we cannot do that using code, we found a tool designed mainly for Yolo imaging called “Yolo Annotation Tool”. This tool enabled us to name objects in photo as a class with their right location by drawing boxes on each object.
- Week 11
Throughout this week, we spent all days working on the training the model. Since we trained our model with the darknet framework and the other team members were not able to run it on their personal computer. We all met and train the models after multiple failures. Darknet requires CUDA API with complex configuration. These configuration steps are even more complex on windows and Macs making it impossible for us to work on a windows for the training. Finally, it was successfully trained without an output which is then copied to the other team members for testing. We wrote code in python to be able to read the output file and also use any video and cam as a data source. This was the hardest part through out the process but we were able to make it work using additional python library called “Cvlib”.
- Week 12
During the end of this session, we met after school to fix every known code error and to also work on our presentation slides for the final project presentations.
We documented the function/s of each code block with screenshot of execution output. We also recorded a video demonstration of how the application work.
- Week 13
This session marks the end of our journey. We presented our project to the lecture.
Special thanks to our Lectures
– Mr. Ford
– Mrs. Nurul
– Mr. Andreas
For their effort and support throughout the journey.
Posted in Uncategorized
Leave a comment
Ethical Hacking & Penetration
Introduction to Ethical Hacking and Penetration Penetration.
This blog covers my path of learning Ethical Hacking & Penetration and, I have listed down all topics in chapters for better understanding. It covers all the basics and offers a tour of Ethical Hacking & Penetration
Posted in Uncategorized
Leave a comment