INFORMATION GATHERING
What is Target Scoping?
Target Scoping is defined as an empirical process for gathering target assessment requirements and characterizing each of its parameters to generate a test plan, limitations, business objectives, and time schedule.
Target Scoping involves the following:
- Gathering Client Requirements – deals with accumulating information about the target environment through verbal or written communication. What is their phone number, address, contact details, etc; What are the penetration test type? Is it black box or white box? What are the devices that should be tested?
- Preparing Test Plan – depends on different sets of variables. These may include shaping the actual requirements into structured testing process, legal agreements, cost analysis, and resource allocation.
- Profiling Test Boundaries – determines the limitations associated with the penetration testing assignment. These can be a limitation of technology, knowledge, or a formal restriction on the client’s IT environment. To make it simple, border that we should not cross.
- Defining Business Objectives – is a process of aligning business view with technical objectives of the penetration testing program. Making sure that we are heading to the right objective and ensuring that the testing output will be a benefit to the business.
- Project Management & Scheduling – directs every other step of the penetration testing process with a proper timeline for test execution. This can be achieved by using a number of advanced project management tools.
Gathering information:
Gather information involves collecting information of the client. This can be the company’s name, locations, contact addresses etc. This process help the pen tester with informations regarding the type of penetration testing to perform. Objective of the testing, devices to test and operating systems to work with. This process is called footprinting in Ethical hacking.
Footprinting which means gathering information about a target system which can be used to execute a successful cyber attack. To get this information, a hacker might use various methods with variant tools. This information is the first road for the hacker to crack a system.
There are two types of footprintying as following below.
- Active Footprinting:
Active footprinting means to perform footprinting by getting in direct touch with the target machine. - Passive Footprinting:
Passive foot printing means collecting information of a system located at a remote distance from the attacker.
Footprinting Tools
- Google – Google is a great tool for information gathering.
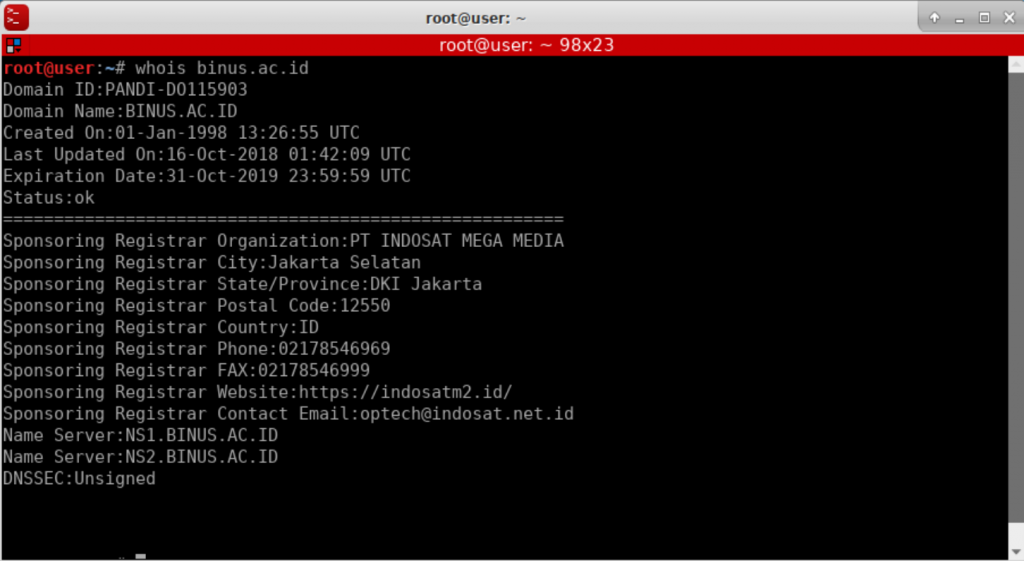
- Whois is a widely used Internet record listing that identifies who owns a domain and how to get in contact with them. Kali Linux comes with whois integration make it easy to get information about a client through the console.
Information Gathering using Footprinting Tools
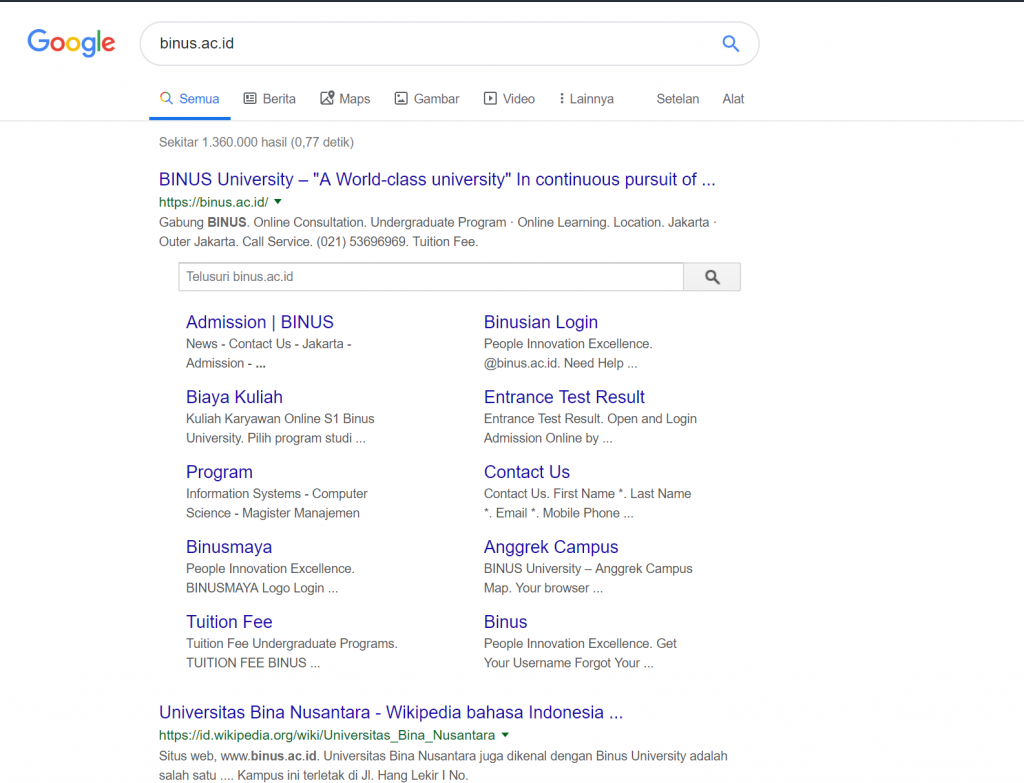
- Google – navigate to google.com and simply enter the information you are seeking e.g binus.ac.id.
- Whois – Gethering information about binus.ac.id. Simply type whois following the domain name. e.g whois binus.ac.id
References
