INFORMATION GATHERING – Enumerating Target
Target Discovery refers to the process of gather ingmore or useful information about a target. The goal of discovery is to start with no information and gather as much data as possible about the target network and systems. We then use this information to identify potential exploits. These can be achieved by using scanning tools like nmap.
Scanning is a set of procedures for identifying live hosts, ports, and services, discovering Operating system and architecture of target system, Identifying vulnerabilities and threats in the network. Network scanning is used to create a profile of the target organization.
Scanning refers to collecting more information using complex and aggressive reconnaissance techniques.
Nmap is a powerful network security tool written by Gordon Lyon. It was released almost 20 years ago (in 1997) and has since become the de facto standard for network mapping and port scanning, allowing network administrators to discover hosts and services on a computer network, and create a map of the network.
Although usually used for port scanning, Nmap offers many additional features:
- Host discovery.
- Operating system detection.
- Service version detection.
- Network information about targets, such as DNS names, device types, and MAC addresses.
- Ability to scan for well-known vulnerabilities.
We will use nmap to see if we can get any information from target machine.
Since scanning can be illegal on some machines, I will perform this test on a domain i am authorized to use.
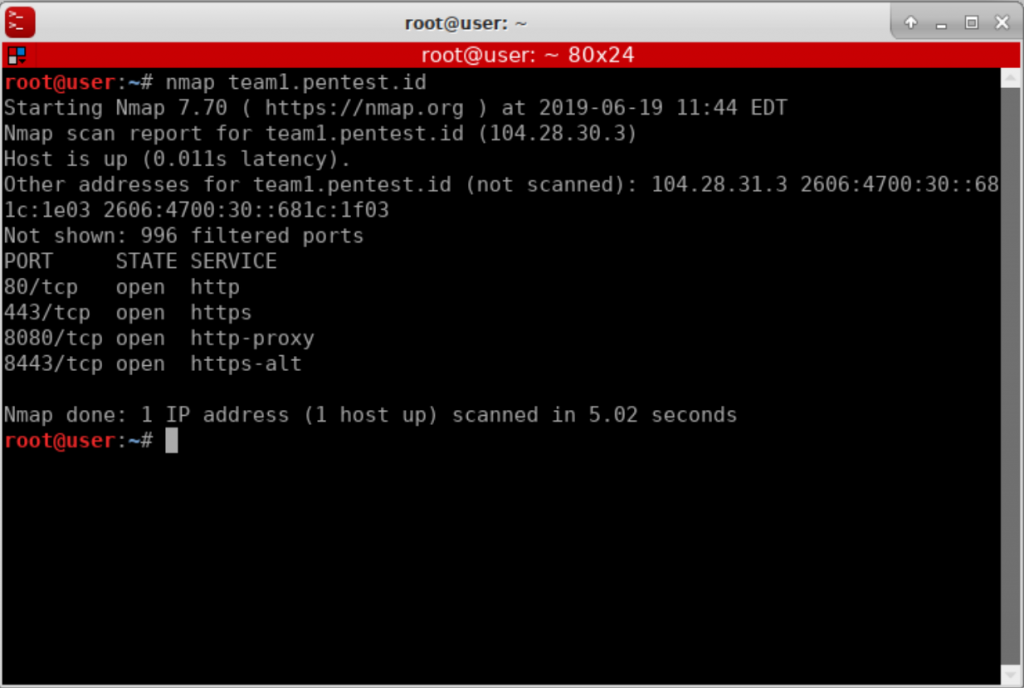
- Running a basic nmap command nmap team1.pentest.id on our target “team1.pentest.id”, we got some basic useful informations like available ports and running services.
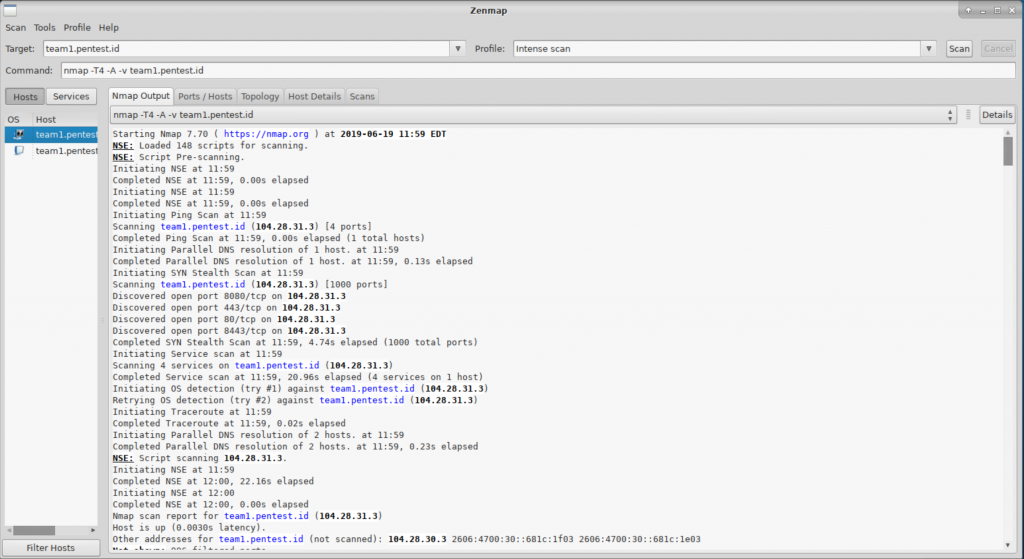
Another tool we can rely on to gather much information is Zenmap.
Zenmap is the official Nmap Security Scanner GUI. It performs the same functions as that of nmap. The only difference is that you get to see everything graphically instead on the console logs provided by nmap.
- Like the previous task, I used zenmap as discovery tool to gather information about my target “team1.pentest.id”, I have got more information about my target with some files available on the server. This result can be achieved if the generated command
nmap -T4 -A -v team1.pentest.id is executed.
-T4 refers to the timing T<0-5> higher is faster
-A refers to enable OS detection.
-v refers to the verbosity level. - This provides discovered ports.
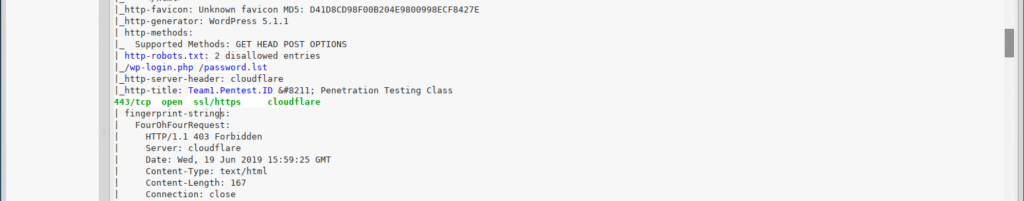
- Open ports, services running and files in the root directory.
References
